Awe-Inspiring Examples Of Tips About How To Check Sql Injection
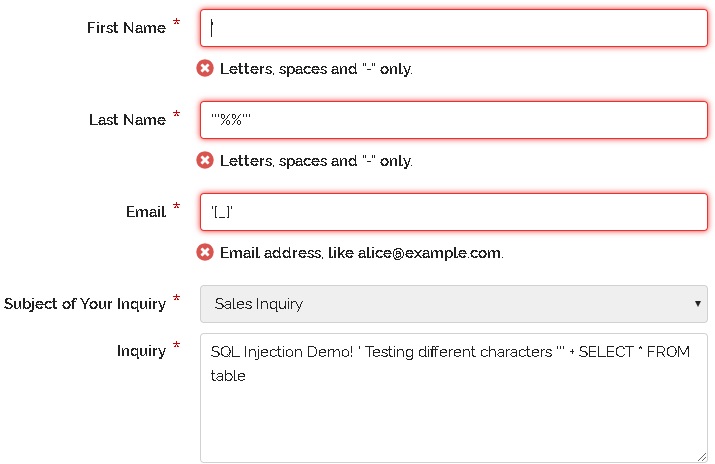
The following script shows a simple sql injection.
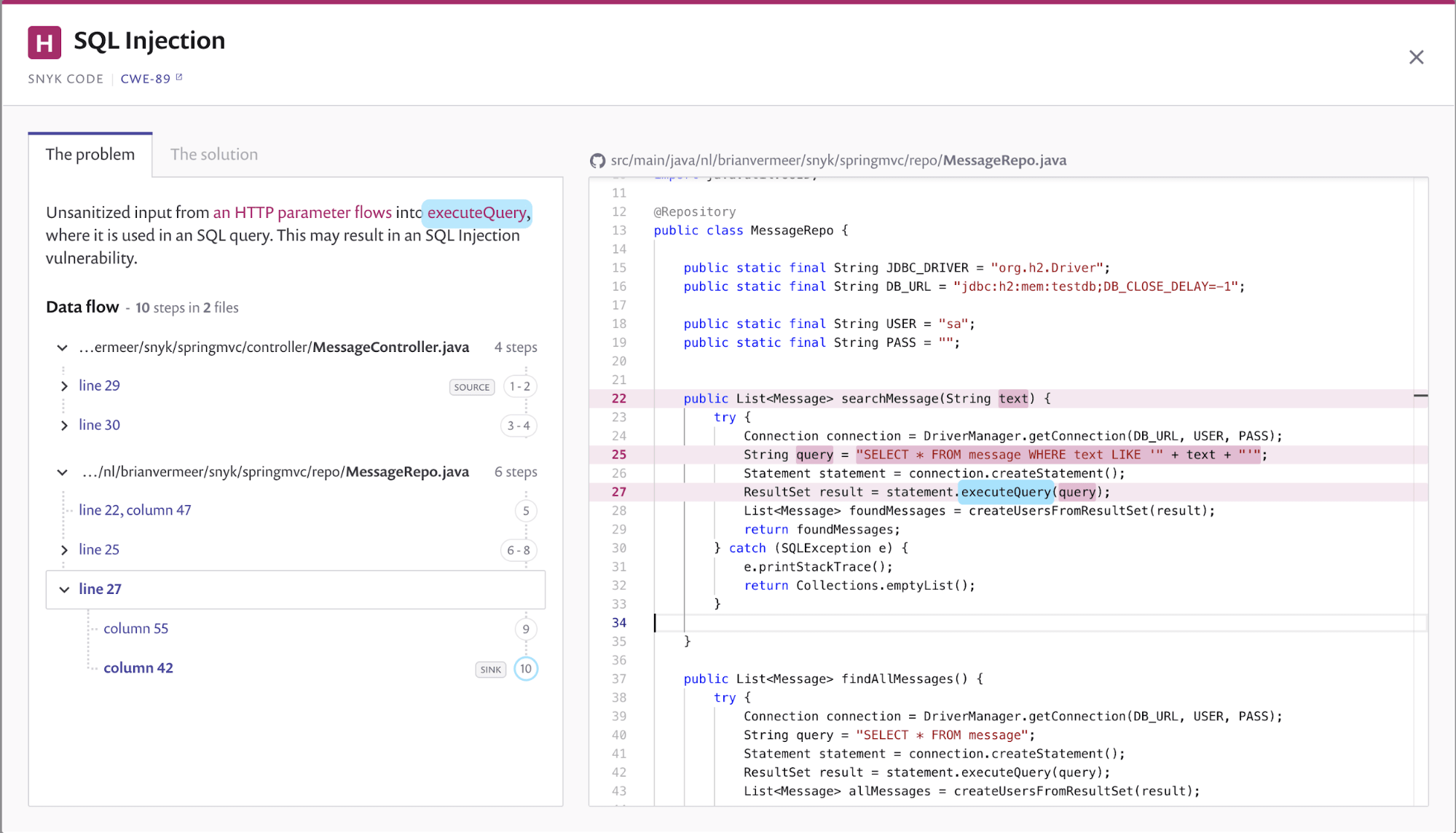
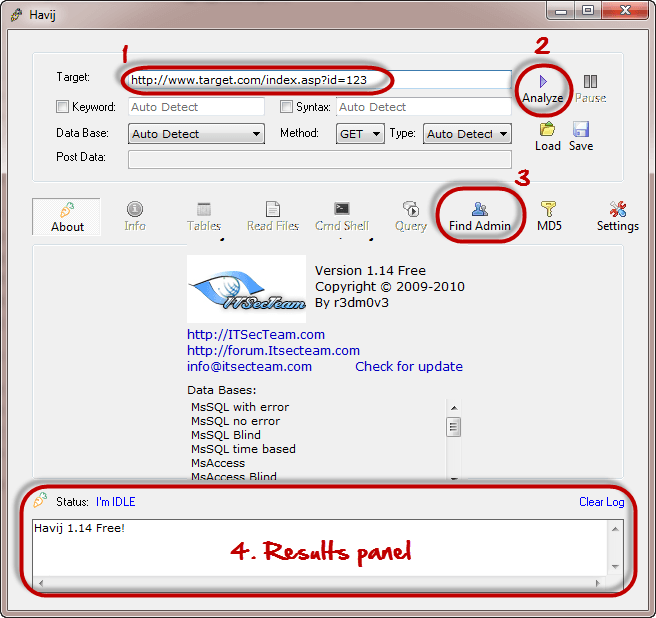
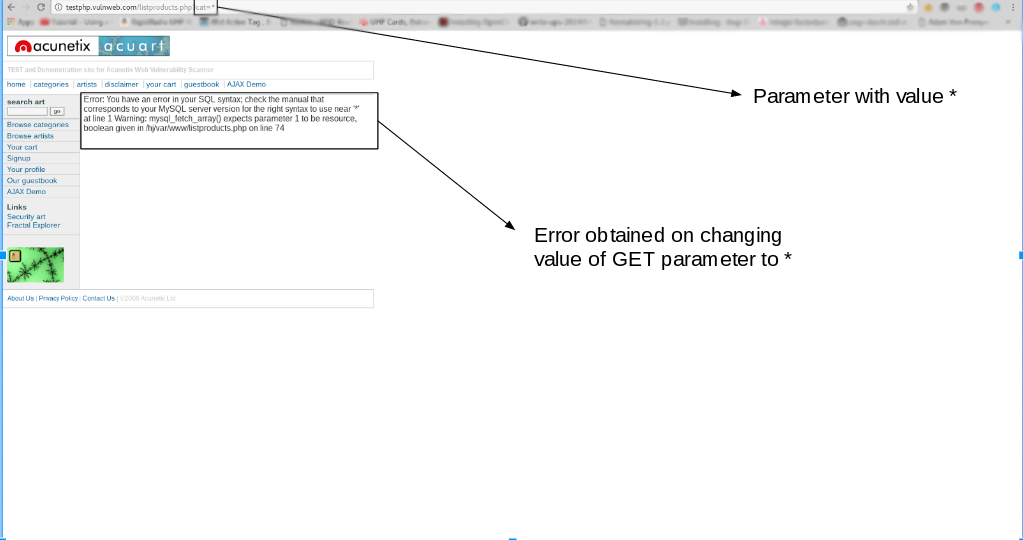
How to check sql injection. In this first step, the scanner tries to identify all the pages within the target web application,. 2 bedroom houses for rent in albany georgia; List information about the existing databases.
Select id, firstname, lastname from authors. Getting unauthorized access to the system using sql injection. It occurs when actors send a crafted sql query to add, extract, delete, or.
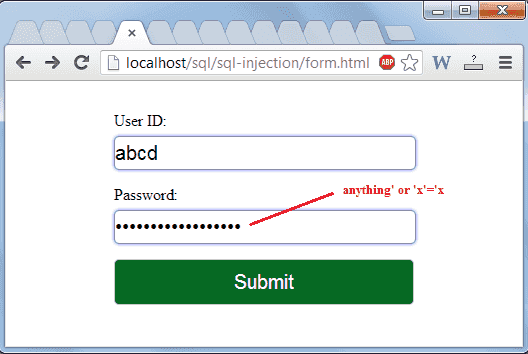
Select * from tbluser where username=‘dummy’ and. Sql injection is a technique threat actors use to attack applications with a database connection. So don’t do this in mysql:
Generally there are three types of sql injection methods: Performing full application security audits can determine the. The online scanner includes two steps:
Delimiter // create procedure `findusers`( in username varchar(50) ) begin. To display sql injection check statistics by using the command line: The above example is a case of boolean based sql injection.
At the command prompt, type: Select id, firstname, lastname from authors. Personalized gifts for someone who lost a loved one;